Relay
- Importing data
Press the import button, also shown as >> when the interface is small, to import data into the list.The following file types are supported:
CSV (Comma delimited) (*.csv)
Text (Tab delimited) (*.txt)
All Files (*.*)
The data should be separated by commas, tab characters or newlines.
Each data entry must match the validation wildcard '*.*.*.*'. Entries that do not match will be discarded.
Duplicate entries are not imported more than once. - Importing data
Press the import button, also shown as >> when the interface is small, to import data into the list.The following file types are supported:
CSV (Comma delimited) (*.csv)
Text (Tab delimited) (*.txt)
All Files (*.*)
The data should be separated by commas, tab characters or newlines.
Each data entry must match the validation wildcard '*.*.*.*'. Entries that do not match will be discarded.
Duplicate entries are not imported more than once.
The Relay page in the SMTP Server is used to prevent Open Relay. Open Relay is when third parties can send email freely through your email system, and hence use your email system to send unsolicited email. Typically if you are an Open Relay you will be blacklisted by one or more of the DNS based Open Relay block lists. For this reason it is crucial that your ensure your server is not an Open Relay. By default Hexamail Vault is configured to prevent Open Relay. This may present problems for your users if they are attempting to send email from your domain using your Hexamail Vault server when on dial-up or from other non-internal IP addresses.
Ensuring your server is not an Open Relay
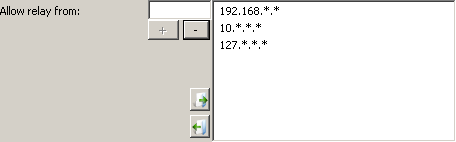
Relay is when a party tries to send an email from outside of your domain to another address outside of your domain using your server. Sending an email is when a party attempts to send an email as if from your domain to an external domain. Both can be considered Open Relay and will get your server blacklisted if these actions are not restricted. (Sending email as if from your domain is just as good as sending from their own domain to many spammers!) The best way to prevent Open Relay is to restrict the IP addresses that are allowed to send or relay email using your server to a small set of internal or trusted IP addresses or ranges. Hexamail Vault comes preconfigured to only allow the most popular internal IP address ranges. In most cases you will not have to make changes. If you know of other specific servers that need to send email through your email server (not incoming email TO your email server, but outgoing email), add their IP addresses to the Allowed Relay IP list. Also, if you use an internal IP range that is not already listed or covered by one of the IP ranges in the list, add your internal IP range. Use the * symbol to mean any, or use a range such as 0-255, e.g. 10.1.*.* means any IP starting with 10.1 If your users may need to send email using your email server, as if from your domain, when they are outside of your office network or LAN, and perhaps on dial-up or other dynamic or unknown IP addresses the best way is to enforce SMTP logins for those users. See the section entitled "Allowing your users to send using your Hexamail Vault server when on dial-up or connected from external locations"
Allowing your users to send using your Hexamail Vault server when on dial-up or connected from external locations
The best way to allow roaming users or users external to your LAN to send email using your Hexamail Vault server is to allow them to authenticate from anywhere to prove who they are. To do this go to the 'Security' page in the SMTP Server pages and add an SMTP login for your roaming users to use. Once they have authenticated they can send email freely using your Hexamail Vault server and the IP address checks are bypassed for the authenticated user. Check the help for the 'Security' page on how your users should configure their email clients to take advantage of this feature.
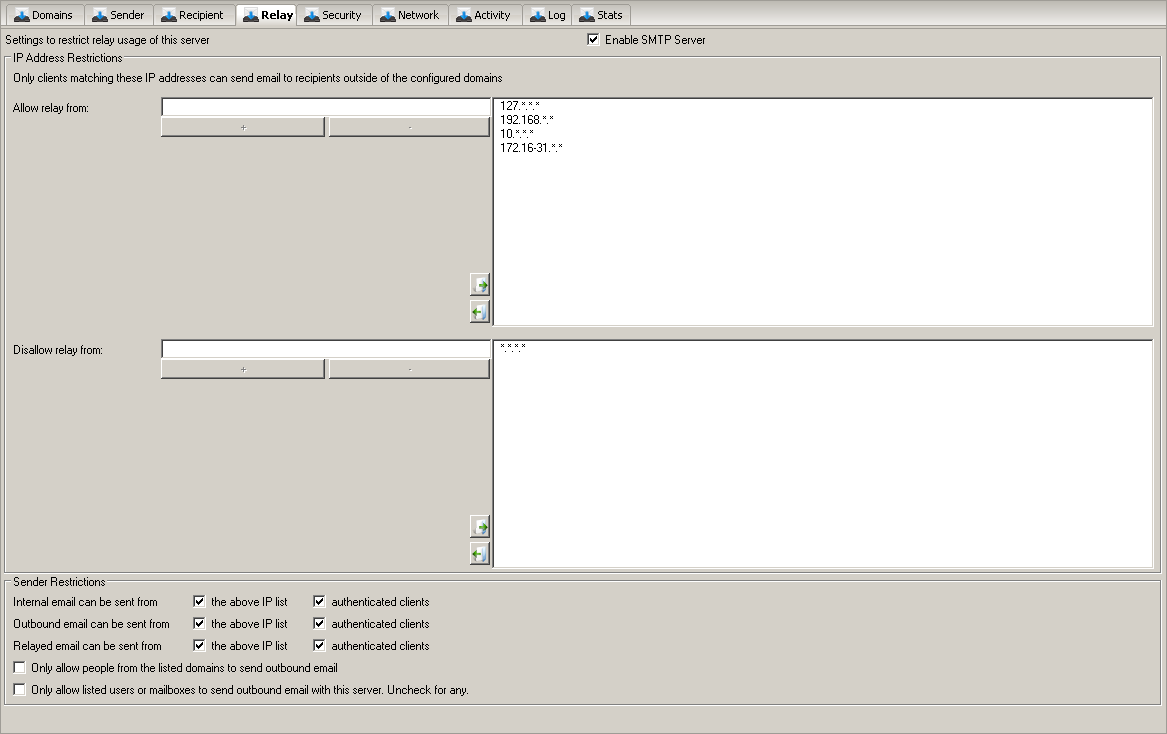
IP Address Restrictions
The default is usually sufficient to allow outgoing email to be sent from your email server, as the typical internal IP ranges (non routed IP ranges) of 192.168.*.*, 10.*.*.* and 172.16-31.*.* are present by default. (NOTE: 172.16-31.*.* is rarely used today)
Sender Restrictions